The Work with Subsystems command, WRKSBS, brings up with Work with Subsystems list screen. By entering 4 next to the subsystem name in the option column and pressing Enter, we can end that subsystem. Entering 5 instead and pressing Enter display’s the subsystem’s description, and entering 8 lets us work with that subsystem’s jobs.
It isn’t difficult to create new subsystems for batch, interactive, or server purposes. A subsystem definition consists of three major components, the subsystem attributes, the work entries, and the routing entries.
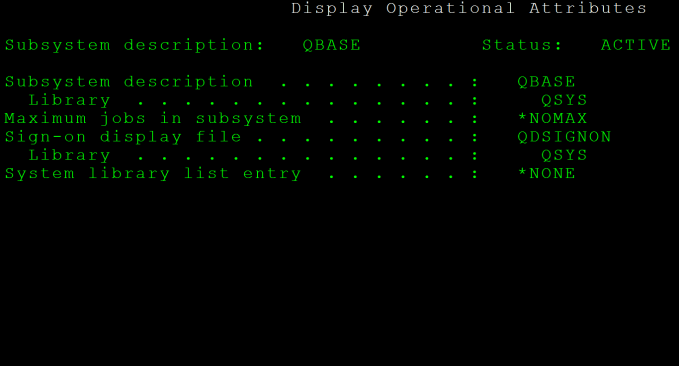
The subsystem description, *SBSD, is an object used to describe a subsystem and to control what tasks the subsystem can perform. Each time a subsystem is created, a subsystem description is required.
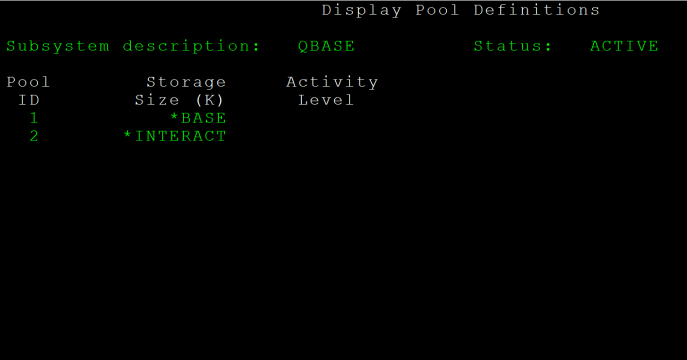
Subsystem attributes comprise the general definition of the subsystem and control its main storage allocations. This general definition includes the subsystem name, library, text description, the maximum number of jobs allowed to run on the subsystem, and the storage pool definitions. Main storage on the IBM i is divided into a number of different storage pools. The storage pool definition has a subsystem either share an existing pool of main storage, establish a private pool of main storage, or both. A private pool is created and named by the subsystem description, and it can only support one subsystem.
The Create Subsystem Description command, CRTSBSD, enables us to create a new subsystem description. Entering CRTSBSD and pressing Enter brings up the Create Subsystem Description screen. The first parameter is used to specify the qualified name of the subsystem description, which is the name of the library and the name of the subsystem itself. This parameter, SBSD, takes *CURLIB by default as the library. The second parameter, POOLS, is used to specify the storage pools used by the subsystem. The activity level for a pool indicates how many jobs on the subsystem can be run in that pool at a given time. A maximum number of 10 storage pools can be assigned to the subsystem. The first pool is used to support the subsystem driver; for performance reasons, this pool should usually be *BASE.
The SBSD and POOLS parameters are the only required parameters when creating a new subsystem description. Thus, we can create a simple subsystem by issuing the command CRTSBSD SBSD(TESTSUB) POOLS((1 *BASE)), which creates a subsystem description in our current library named TESTSUB that uses the shared *BASE storage pool. We can then issue the command DSPSBSD SBSD(TESTSUB) to view the attributes of the TESTSUB subsystem description. At the top of the screen we will seen the name, library, and status of this subsystem description; as we can easily see, the subsystem’s status is INACTIVE.
The Maximum Jobs parameter, MAXJOBS, specifies the maximum number of jobs that can be run on the subsystem at any one time. We can put *NOMAX here to indicate that there is no limit to the number of jobs that can be run at once on the subsystem. In practice, it is often good to set a number here, to prevent the subsystem from potentially being flooded. Note the difference between Maximum Jobs and the Activity Level, the Maximum Jobs parameter specifies how many jobs are in the system, whereas Activity Level specifies how many of those jobs are actually working at one time.
Finally, the Text parameter, TEXT, enables us to give a text description for the subsystem. Both the MAXJOBS and TEXT parameters are optional; by default, MAXJOBS is set to *NOMAX and TEXT is set to *BLANK.
Let’s create a second subsystem named TESTSUB2. We will give this subsystem two storage pools, and set the maximum number of jobs to 15. Issuing the command CRTSBSD SBSD(TESTSUB2) POOLS((1 *BASE) (2 65536 8)) MAXJOBS(15) creates our second subsystem, with a secondary storage pool of 64K that can run eight jobs at once. Entering the command DSPSBSD SBSD(TESTSUB2) displays the subsystem description, which, like TESTSUB1, is inactive. Selecting option 2 will display the storage pools, of which there are two, just as we defined.
Subsystems do not become active until they are started. A subsystem definition is, in the end, only a definition of what resources should be allocated; to allocate the resources, we must activate the subsystem. We can activate a subsystem using the Start Subsystem command, STRSBS. The only parameter that must be specified is the subsystem to start, SBSD. If the subsystem is in a library that is in our library list, we can can omit the library name, otherwise we should include the library name before the name of the subsystem.
Let’s start our TESTSUB subsystem by issuing the command STRSBS SBSD(TESTSUB). Entering the command DSPSBSD SBSD(TESTSUB) will then show us that the subsystem is active. Let’s also start the second subsystem we have defined, TESTSUB2, by entering the command STRSBS SBSD(TESTSUB2). Note that as both TESTSUB and TESTSUB2 were created in our current library, *CURLIB, which is part of our library list, we do not have to insert the library name.
Use the End Subsystem command, ENDSBS, to shut down a subsystem. Typing in ENDSBS at the command line, we can press F4 to prompt for parameters. The system will prompt us for the name of the subsystem we want to end, and whether we want a controlled end, signified by *CNTRLD, or an immediate end, signified by *IMMED.
A controlled end, *CNTRLD, allows all active jobs to continue for a set period defined in seconds in the DELAY parameter. We can change the value of the Delay Time parameter, DELAY, to a given number of seconds, or, alternately, we can specify no maximum with *NOLIMIT, which lets active jobs continue indefinitely.
An immediate end to a subsystem, *IMMED, forces the system to take drastic measures to end jobs. If the jobs were updating files, especially keyed files, the IBM i operating system may have to repair the files the next time we IPL, which could incur a significant time penalty.
Let’s end the TESTSUB subsystem via the command ENDSBS SBS(TESTSUB) OPTION(*IMMED); this command will immediately shut down the TESTSUB subsystem. We can use the *IMMED option, as we know that there are no jobs being run in the TESTSUB subsystem. We’ll end the TESTSUB2 subsystem using a controlled end and a time delay of 180 seconds by issuing the command ENDSBS SBS(TESTSUB2) OPTION(*CNTRLD) DELAY(180).
We can also use the End Subsystem Option parameter, ENDSBSOPT, to improve the performance of ending subsystems. If we specify ENDSBSOPT(*NOJOBLOG), the subsystem will end without producing a job log for every job that was running in the subsystem, which can potentially save system resources. If we specify ENDSBSOPT(*CHGPTY *CHGTSL), the run priority and time slice for all jobs in the subsystem that end will be modified so as to consume less system resources than jobs that are still running in other subsystems.
All parameters specified on the Create Subsystem Description screen may be modified with the Change Subsystem Description command, CHGSBSD. Let’s start by issuing the command CGHSBSD SBSD(*CURLIB/TESTSUB) MAXJOBS(10); this command will alter the TESTSUB subsystem to have a maximum number of 10 jobs. We can then enter DSPSBSD SBDSD(TESTSUB) and then select option 1 to verify that the maximum number of jobs has been altered. Next, let’s modify the TESTSUB2 subsystem so that it has a third storage pool with approximately 32K of storage and an activity level of 5. To do this, we issue the command CHGSBSD SBSD(TESTSUB2) POOLS( (3 32000 5)).
We can then start up both subsystems by issuing the commands STRSBS SBSD(TESTSUB) and STRSBS SBSD(TESTSUB2). Next, let’s end the TESTSUB subsystem immediately and without writing job logs by entering the command ENDSBS SBS(TESTSUB) OPTION(*IMMED) ENDSBSOPT(*NOJOBLOG). Then, let’s end the TESTSUB2 subsystem with a six minute delay, no job log, and with jobs that will compete less aggressively for processor cycles than jobs running in other subsystems. To do this, enter the command ENDSBS SBS(TESTSUB2) OPTION(*CNTRLD) DELAY(360) ENDSBSOPT(*NOJOBLOG *CHGPTY *CHGTSL).
Finally, we need to be able to remove subsystem descriptions that we no longer need. To delete a subsystem description, we use the Delete Subsystem Description command, DLTSBSD. To delete TESTSUB and TESTSUB2, we issue the commands DLTSBSD SBSD(TESTSUB) and DLTSBSD SBSD(TESTSUB2). Please be aware that the associated subsystem must be inactive before it is deleted.
Wanting to get the most out of your IBM i investment? Take a look atwww.laservault.com, the friendly IBM backup solution.